|
| Credit: Patrick Tomasso |
If you're returning rows from a spreadsheet or a SharePoint list, you normally use an "Apply to each" action to pull out the data.
But when you use "Apply to each" the entire row is pulled into memory and this can be slow, especially if you've got a lot of columns.
If there is only one row this isn't necessary; instead you can use the "First" expression, which is much quicker as it just loads a specific column value rather than the whole row.
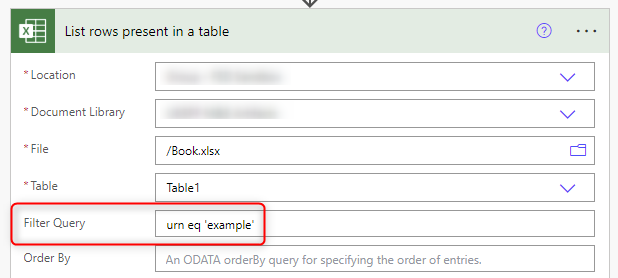
Let's say you're filtering on a unique refeerence number column called "URN" to return a specific row using an OData Filter Query, such as urn eq 'example', and you want to get the value of a column from that row called "Start Date".
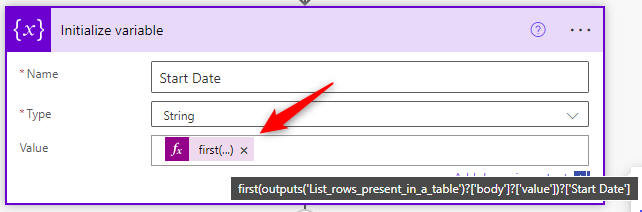
Rather than using "Apply to each" to pull the value out, use the following expression in a Compose or Set Variable action:
First(outputs('List_rows_present_in_a_table')?['body']?['value'])?['Start Date']